

You have several Conditional Access policies that block noncompliant devices from connecting to services.
You need to identify which devices are blocked by which policies.
What should you use?
Correct Answer:
B
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
✑ Source Anchor: objectGUID
✑ Password Hash Synchronization: Disabled
✑ Password writeback: Disabled
✑ Directory extension attribute sync: Disabled
✑ Azure AD app and attribute filtering: Disabled
✑ Exchange hybrid deployment: Disabled
User writeback: Disabled -
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Azure AD app and attribute filtering settings.
Does that meet the goal?
Correct Answer:
B
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
✑ Source Anchor: objectGUID
✑ Password Hash Synchronization: Disabled
✑ Password writeback: Disabled
✑ Directory extension attribute sync: Disabled
✑ Azure AD app and attribute filtering: Disabled
✑ Exchange hybrid deployment: Disabled
✑ User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Password Hash Synchronization settings.
Does that meet the goal?
Correct Answer:
A
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
✑ Source Anchor: objectGUID
✑ Password Hash Synchronization: Disabled
✑ Password writeback: Disabled
✑ Directory extension attribute sync: Disabled
✑ Azure AD app and attribute filtering: Disabled
✑ Exchange hybrid deployment: Disabled
✑ User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Source Anchor settings.
Does that meet the goal?
Correct Answer:
B
🗳️
HOTSPOT -
You have a Microsoft 365 subscription that uses a default domain name of contoso.com.
The multi-factor authentication (MFA) service settings are configured as shown in the exhibit. (Click the Exhibit tab.)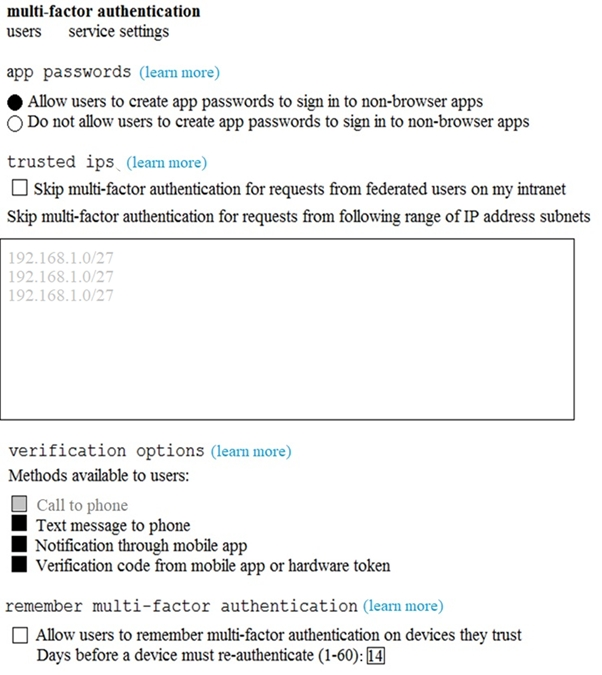
In contoso.com, you create the users shown in the following table.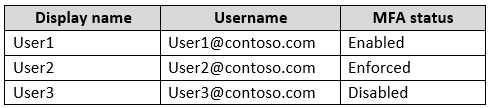
What is the effect of the configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: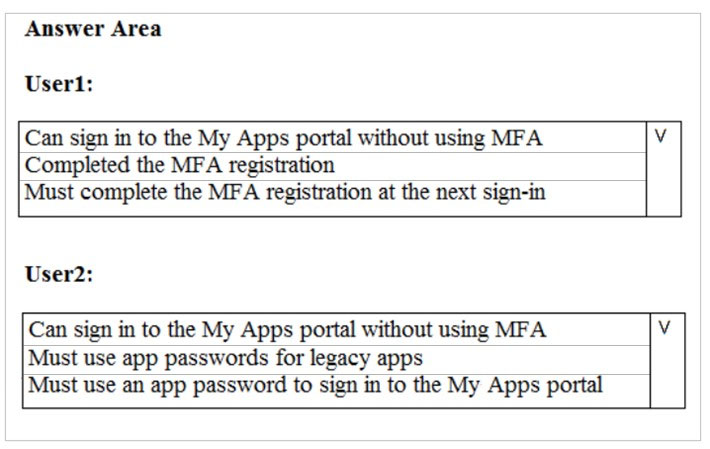
Correct Answer:
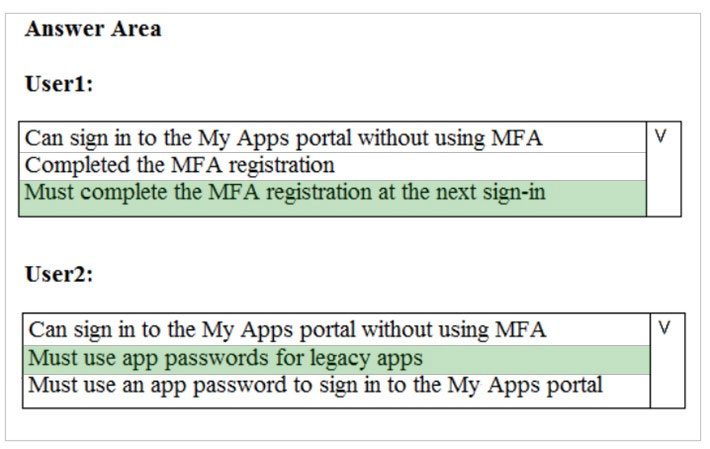
References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates
HOTSPOT -
You configure Microsoft Azure Active Directory (Azure AD) Connect as shown in the following exhibit.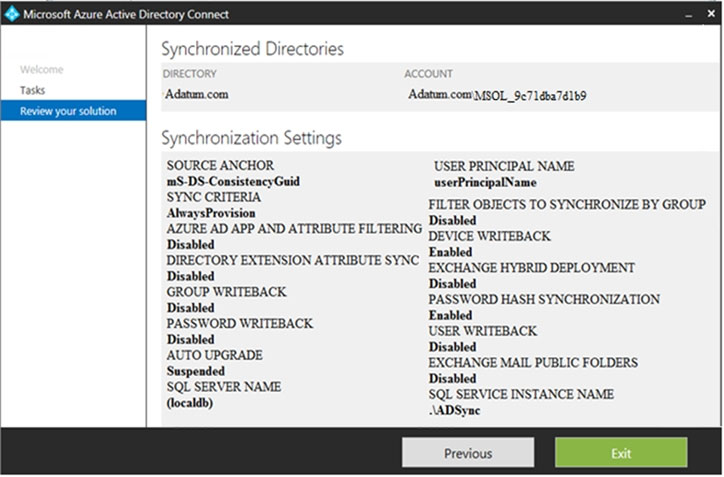
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
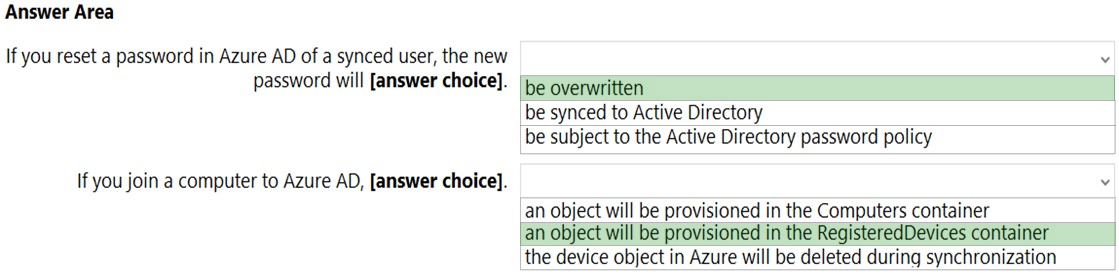
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-device-writeback
You have a hybrid Microsoft 365 environment. All computers run Windows 10 and are managed by using Microsoft Endpoint Manager.
You need to create a Microsoft Azure Active Directory (Azure AD) conditional access policy that will allow only Windows 10 computers marked as compliant to establish a VPN connection to the on-premises network.
What should you do first?
Correct Answer:
A
🗳️
You have a Microsoft 365 subscription.
From the Microsoft 365 admin center, you create a new user.
You plan to assign the Reports reader role to the user.
You need to view the permissions of the Reports reader role.
Which admin center should you use?
Correct Answer:
B
🗳️
You have a Microsoft 365 E5 subscription.
You need to ensure that users who are assigned the Exchange administrator role have time-limited permissions and must use multi-factor authentication (MFA) to request the permissions.
What should you use to achieve the goal?
Correct Answer:
B
🗳️
Your company has a Microsoft 365 subscription.
The company does not permit users to enroll personal devices in mobile device management (MDM).
Users in the sales department have personal iOS devices.
You need to ensure that the sales department users can use the Microsoft Power BI app from iOS devices to access the Power BI data in your tenant.
The users must be prevented from backing up the app's data to iCloud.
What should you create?
Correct Answer:
B
🗳️