

I am configuring the security policy for my JMS module. I am specifying some security conditions for the module.
Which two security conditions are valid in this context? (Choose two.)
Correct Answer:
AD
🗳️
There are two security conditions:
* time-constrained
* By Group or User
Reference:
http://docs.oracle.com/html/E24401_02/taskhelp/jms_modules/modules/ConfigureJMSModuleSecurityPolicies.html
Review the digital certificate below.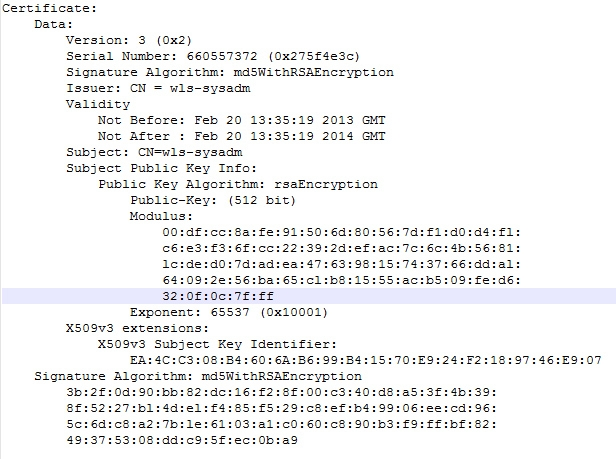
Based on what the certificate contains, which statement is true? (Choose the best answer.)
Correct Answer:
A
🗳️
Incorrect Answers:
C: This is 512-bit Public Key, not a private key.
Note: The subject key identifier extension provides a means of identifying certificates that contain a particular public key.
You want to create a WebLogic Server (WLS) Work Manager with a Response Time Request Class of one second. You start to create the following WLST script: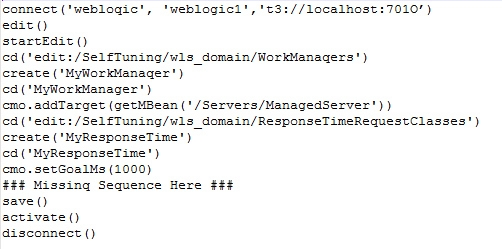
Which two can replace the missing sequence to finish this script? (Choose two.)
Correct Answer:
AD
🗳️
Reference:
http://docs.oracle.com/cd/E12839_01/apirefs.1111/e13952/pagehelp/J2EEappworkresponsetimerequestclassconfigtitle.html
You are creating and configuring a production WebLogic Server (WLS) domain that is highly available. Which three WebLogic Server features allow you to best accomplish this requirement? (Choose three.)
Correct Answer:
BCE
🗳️
B Load balancing is the even distribution of jobs and associated communications across the computing and networking resources in your environment.
C: In a WebLogic Server cluster, application processing can continue when a server instance fails.
E: Migration in WebLogic Server is the process of moving a clustered WebLogic Server instance or a component running on a clustered instance elsewhere if failure occurs. This is called Whole-server migration.
Reference:
http://docs.oracle.com/cd/E23943_01/core.1111/e10106/aa.htm#ASHIA4083