

SIMULATION -
SWITCH.com is an IT company that has an existing enterprise network comprised of two layer 2 only switches; DSW1 and ASW1. The topology diagram indicates their layer 2 mapping. VLAN 20 is a new VLAN that will be used to provide the shipping personnel access to the server. Corporate polices do not allow layer 3 functionality to be enabled on the switches. For security reasons, it is necessary to restrict access to VLAN 20 in the following manner:
✑ Users connecting to VLAN 20 via port f0/1 on ASW1 must be authenticated before they are given access to the network. Authentication is to be done via a
Radius server:
- Radius server host: 172.120.40.46
- Radius key: rad123
- Authentication should be implemented as close to the host as possible.
✑ Devices on VLAN 20 are restricted to the subnet of 172.120.40.0/24.
- Packets from devices in the subnet of 172.120.40.0/24 should be allowed on VLAN 20.
- Packets from devices in any other address range should be dropped on VLAN 20.
- Filtering should be implemented as close to the server farm as possible.
The Radius server and application servers will be installed at a future date. You have been tasked with implementing the above access control as a pre-condition to installing the servers. You must use the available IOS switch features.
Note: Named access list is not supported.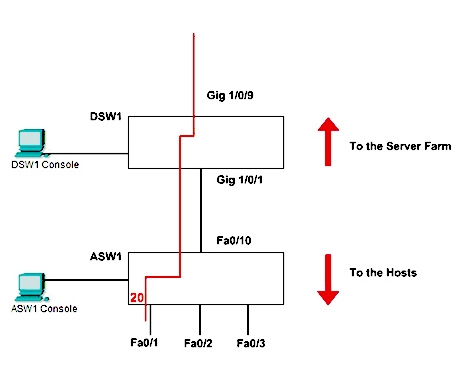

Boek
Highly Voted 6 years, 3 months agoBoek
Most Recent 6 years, 3 months agoAlex
6 years, 4 months agoJothi
6 years, 3 months ago