

A remote user (User1) is unable to reach a newly provisioned corporate windows workstation. The system administrator has been given the following log files from the VPN, corporate firewall and workstation host.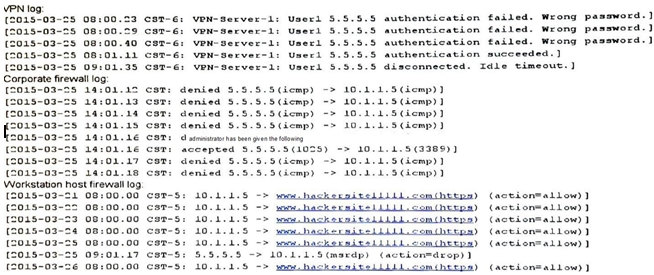
Which of the following is preventing the remote user from being able to access the workstation?
ctux
Highly Voted 5 years, 7 months agoZen1
5 years, 4 months agoDante_Dan
Highly Voted 5 years, 2 months agoMiltduhilt
Most Recent 4 years, 4 months agoCstleafsz
4 years, 5 months agohlwo
4 years, 8 months agoDookyBoots
4 years, 8 months agoSandmanWeB
4 years, 8 months agopokemonmoon
4 years, 9 months agocoentror
4 years, 9 months agoFastiff
4 years, 10 months agoTeza
4 years, 9 months agomichaelcook80
4 years, 11 months agobugabum
4 years, 11 months agoZZZZZZZZZZZZ
5 years agoxiaoyi
5 years agoMelvinJohn
5 years, 2 months agothebottle
5 years, 3 months agoMelvinJohn
5 years, 4 months ago