

While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device.
Given the table below: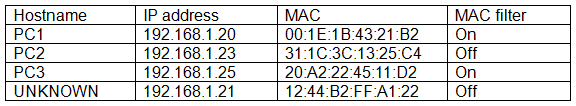
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
jfkqobum
Highly Voted 3 years, 11 months agoSophyQueenCR82
Most Recent 2 years, 1 month agofonka
3 years, 9 months agoDion79
3 years, 10 months agoSamwell21
3 years, 11 months agotroxel
3 years, 10 months agoMistermiyagi
3 years, 11 months ago