

A security analyst reviews the following output: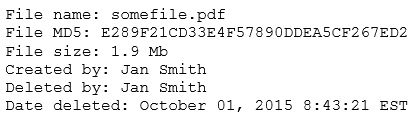
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following: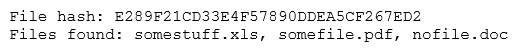
Which of the following is the MOST likely cause of the hash being found in other areas?
Jovo
Highly Voted 5 years, 4 months agosquareskittles
4 years, 11 months agoHuh
4 years, 4 months agoDedutch
4 years, 2 months agoupgrayedd
Highly Voted 5 years, 1 month agoClintBeavers
5 years agostudy_Somuch
4 years, 12 months agoDedutch
4 years, 2 months agoaosroyal
Most Recent 4 years, 3 months agowho__cares123456789___
4 years, 5 months agodinosan
4 years, 10 months agoMagicianRecon
4 years, 11 months agoGerarigneel
5 years, 4 months agostoda
5 years, 4 months agoGMO
5 years, 4 months agoLains2019
5 years, 6 months agomomunah
5 years, 6 months agoJasonbelt
4 years, 10 months ago